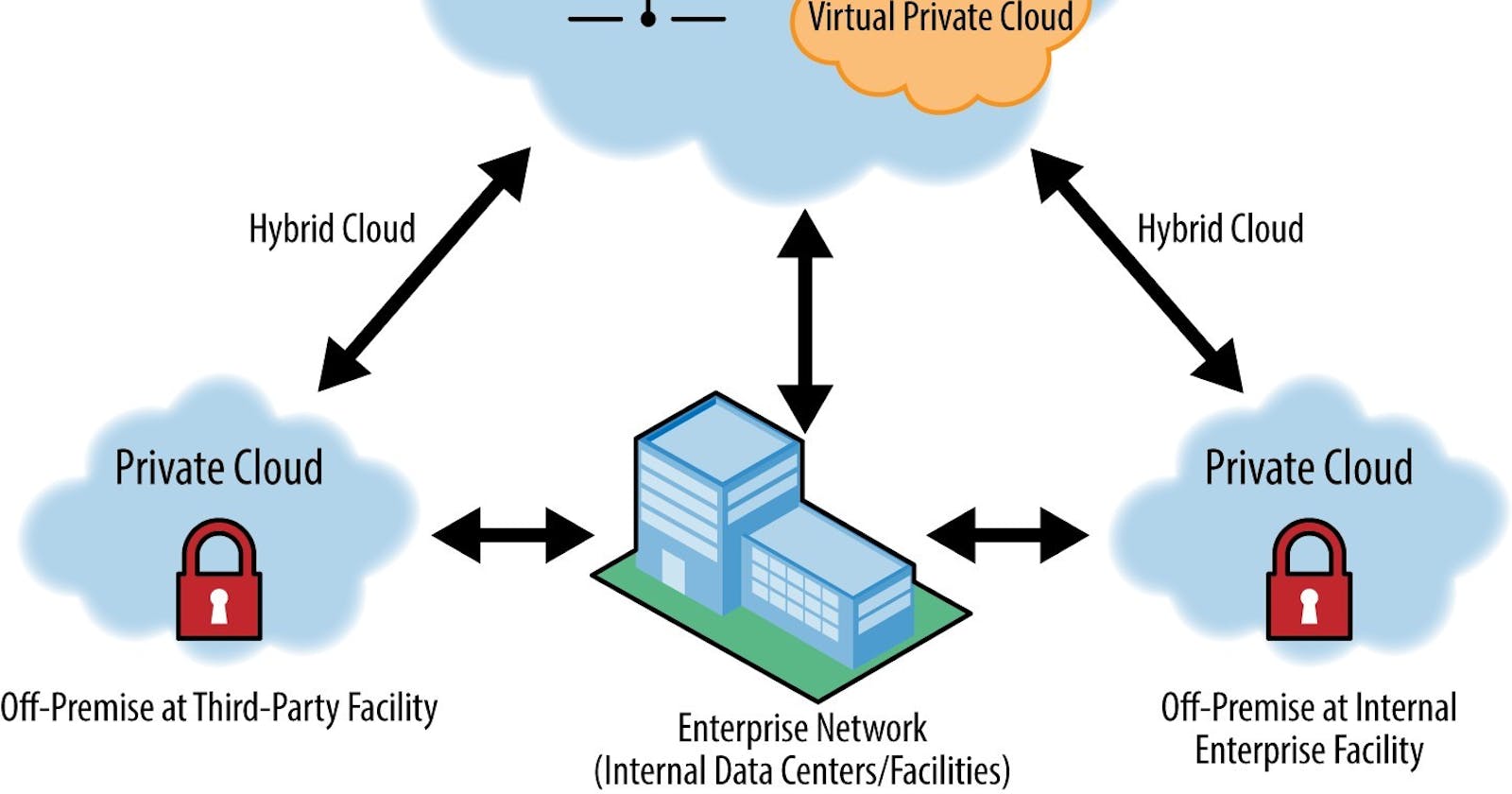
First, Let's understand what is PUBLIC, PRIVATE & VIRTUAL PRIVATE CLOUD.
Let’s Suppose you want to Live in a some House, but you don’t have any house.
Now, you have multiple options :-
1) Either go to a person who owns ‘Residential apartment building’ and pay him monthly rent and live there as a tenant.
2) OR you can purchase your own land and build your own Home on that land.
So In first case, the person who owns ‘residential apartment building’ is a CLOUD PROVIDER (like Google, Amazon, Microsoft)
if you want to live as a tenant in that Residential apartment – it means you are using PUBLIC CLOUD (You are paying and using the services (here some room or apartment allocated to you)). But Other tenants or families also stay in same building and using services.
If you want to purchase your own land and built your own Home there – then it’s a PRIVATE CLOUD You own this. No one can enter into your home.
Then what is VIRTUAL PRIVATE CLOUD ?
In 2nd case, where you are paying monthly rent to ‘residential apartment building owner’. You live in a apartment, but your can share the apartment with your room-mates and KEY of all rooms is shared among your room-mates.
But, If you want a separate room (private) in same apartment i.e. key of that particular room is only with you, no one can enter that room. (neither your family members) That is VIRTUAL PRIVATE CLOUD (a room in PUBLIC CLOUD, but it act as a PRIVATE). Now it’s up to you – to whom you allow into that room and you can control it.
NOTE Private cloud and virtual private cloud are sometimes—and mistakenly—used interchangeably. In fact, a virtual private cloud is actually a public cloud offering.
A private cloud is a single-tenant cloud environment owned, operated, and managed by the enterprise, and hosted most commonly on-premises or in a dedicated space or facility.
A VPC is hosted on multi-tenant architecture, but each customer’s data and workloads are logically separate from those of all other tenants. The cloud provider is responsible for ensuring this logical isolation.
Time to See all these in Practical
- First we will create 3 Virtual Networks.
- Then we will apply Some Firewall rules on all these virtual networks.
- Then we will deploy some virtual machine in all virtual networks.
- Then we will try to connect with each virtual network/Virtual Machine of other network.
Let's see how to create Virtual Network in GCP
- Open and Logged in cloud.google.com
- Navigate to Navigation menu > VPC network > VPC networks.
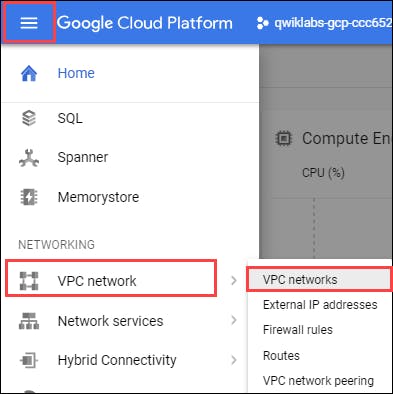
- Click on it, one window will open, we will see default network. Each Google Cloud project starts with the default network
Click Create VPC Network.
Set the Name to managementnet.
For Subnet creation mode, click Custom.
Property Value (type value or select option as specified)
Name managementsubnet-us Region us-central1 IP address range 10.130.0.0/20
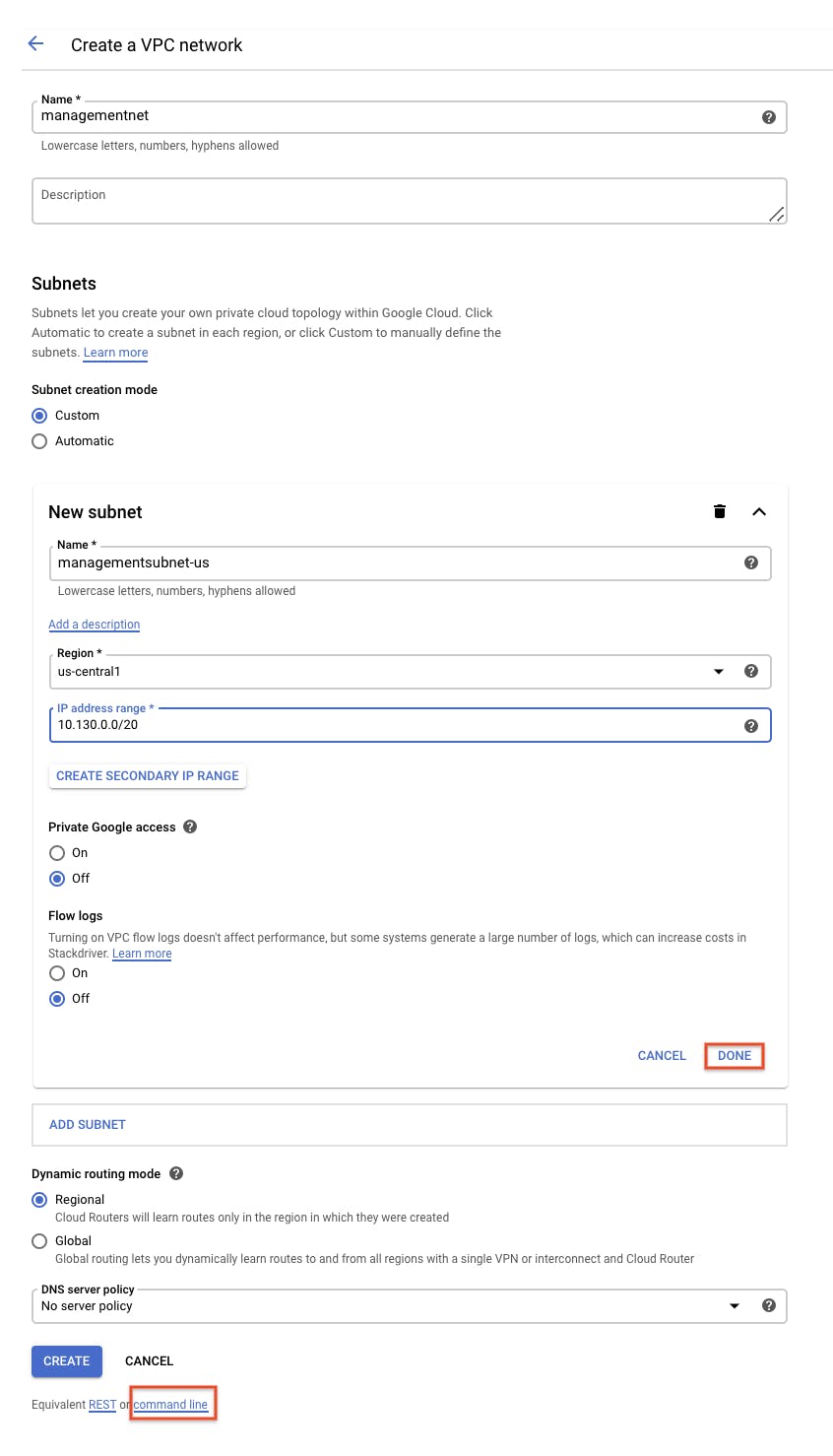
Now you have 2 options - Either Click on CREATE (to create GUI) or Create Commands by clicking on 'Command Line' - It will display command, and you can manual run all those commands. The purpose is same.
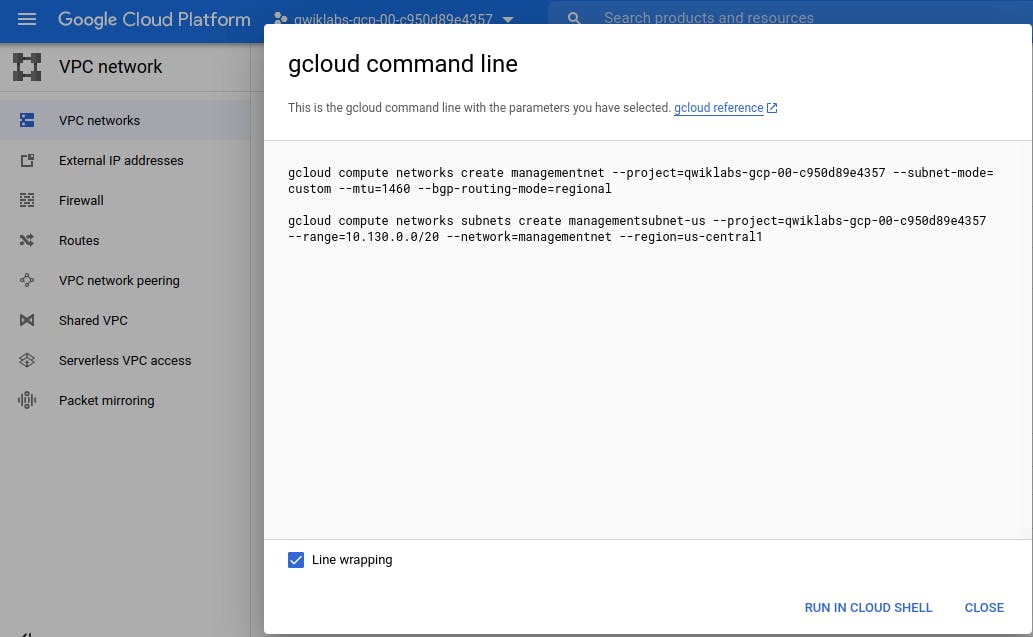
Let's close this window, and click on 'CREATE' button.
Next virtual network we will create using command (Though we can create using GUI as we created 'managementnet)
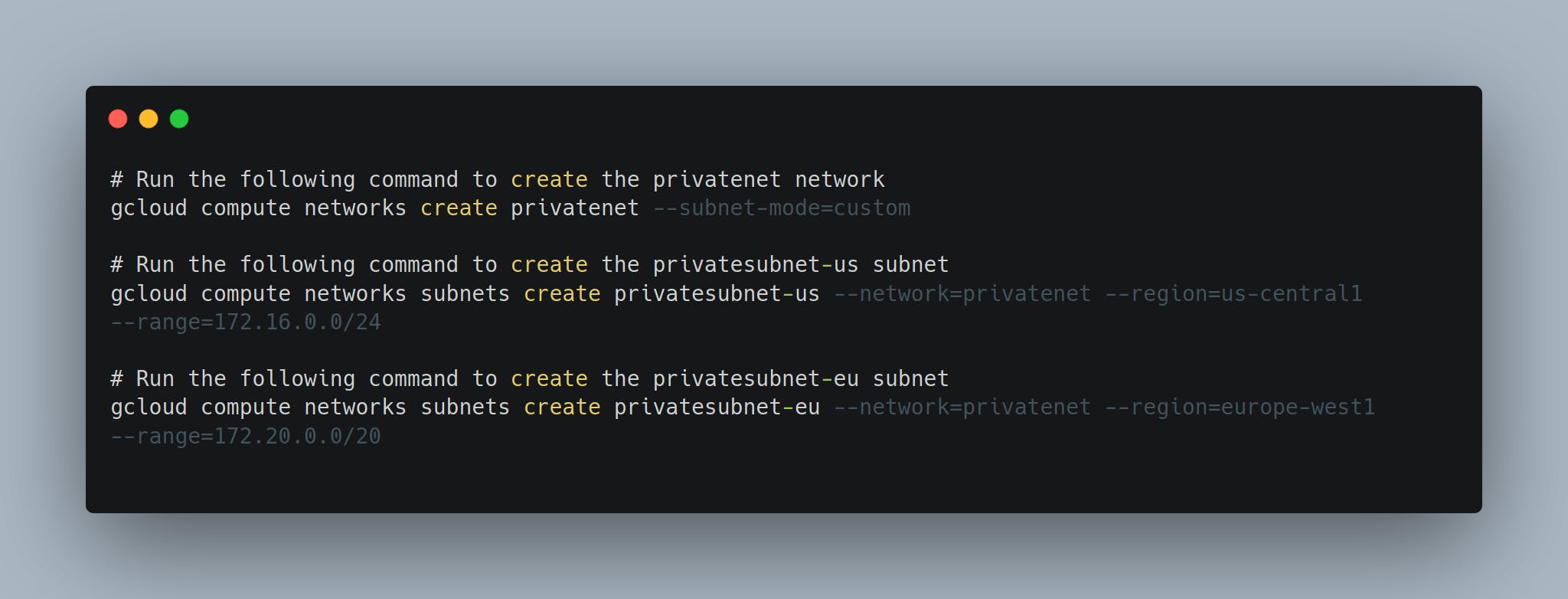
Let's create 2nd Virtual Network - 'privatenet'
In 'privatenet' ==> we will add 2 subnet (one is of US and other is of Europe)
Run all the below 3 commands one by one on - Cloud Terminal.
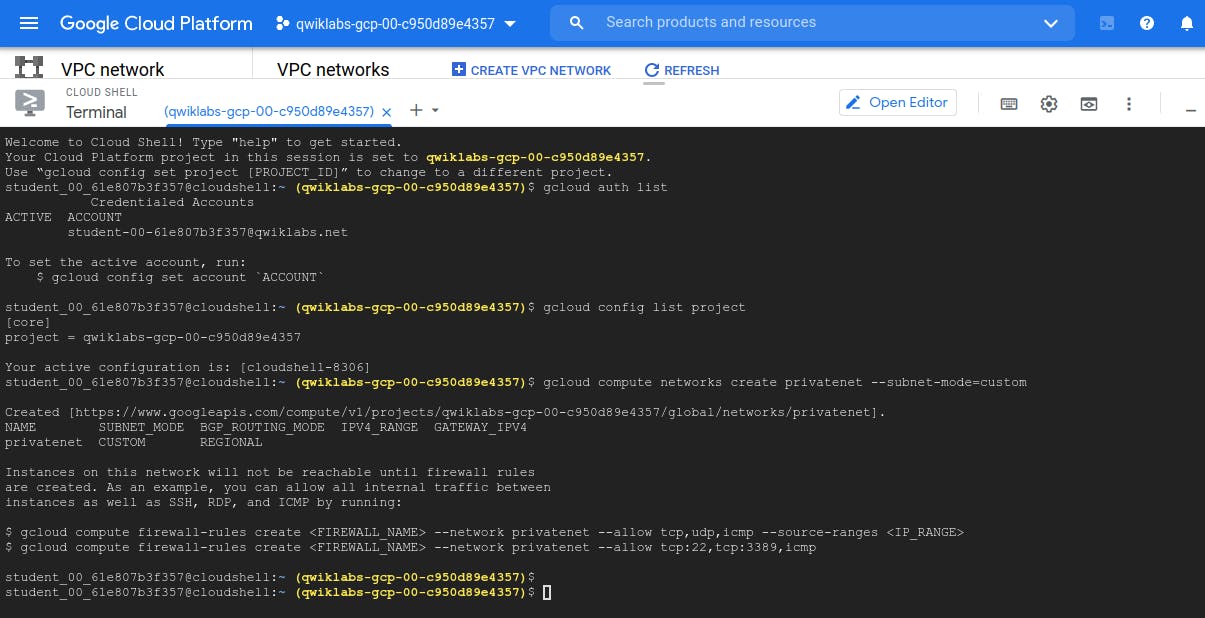
Now, we can see 2 Virtual network (managementnet and privatenet in custom mode) created by us. default (is google cloud default network) and mynetwork (also created by us) - by mynetwork is in Auto Mode (i.e. it automatically pick subnet)
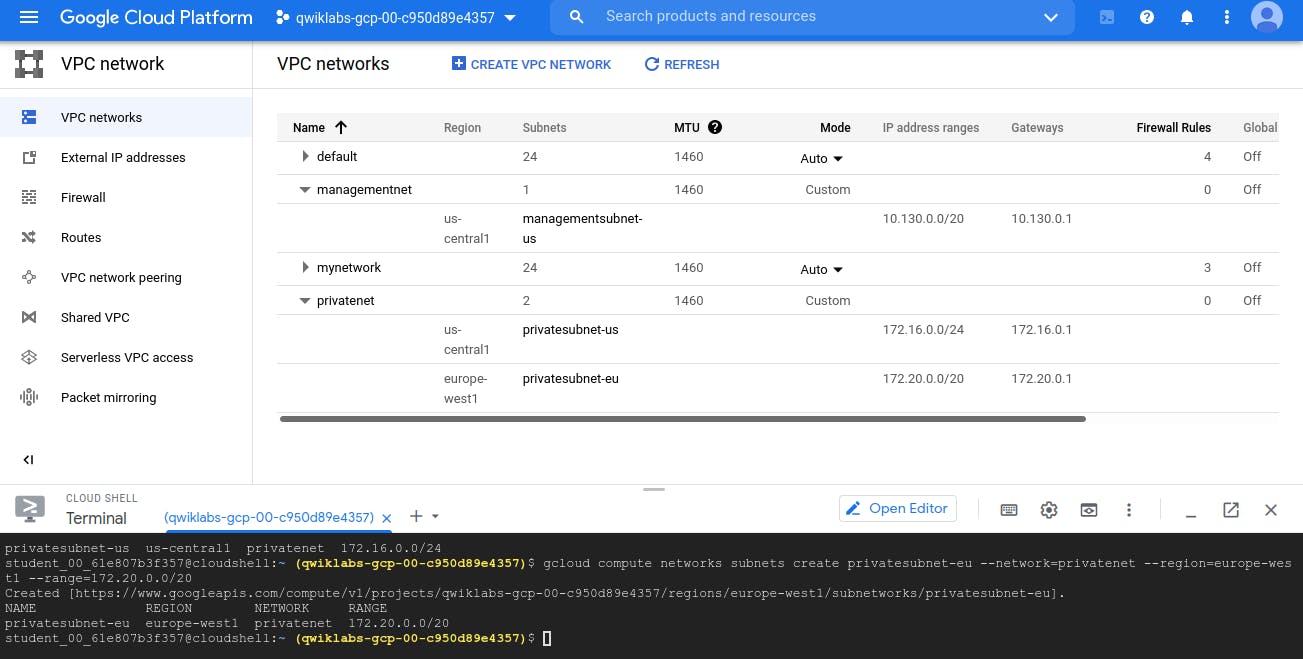
But till now we just created networks, There are no firewall linked with 'managementnet' and 'privatenet' - Thus in above image we see '0' value under firewall column.
We can use commands as well to see all available virtual network and subnets. Below are the commands.
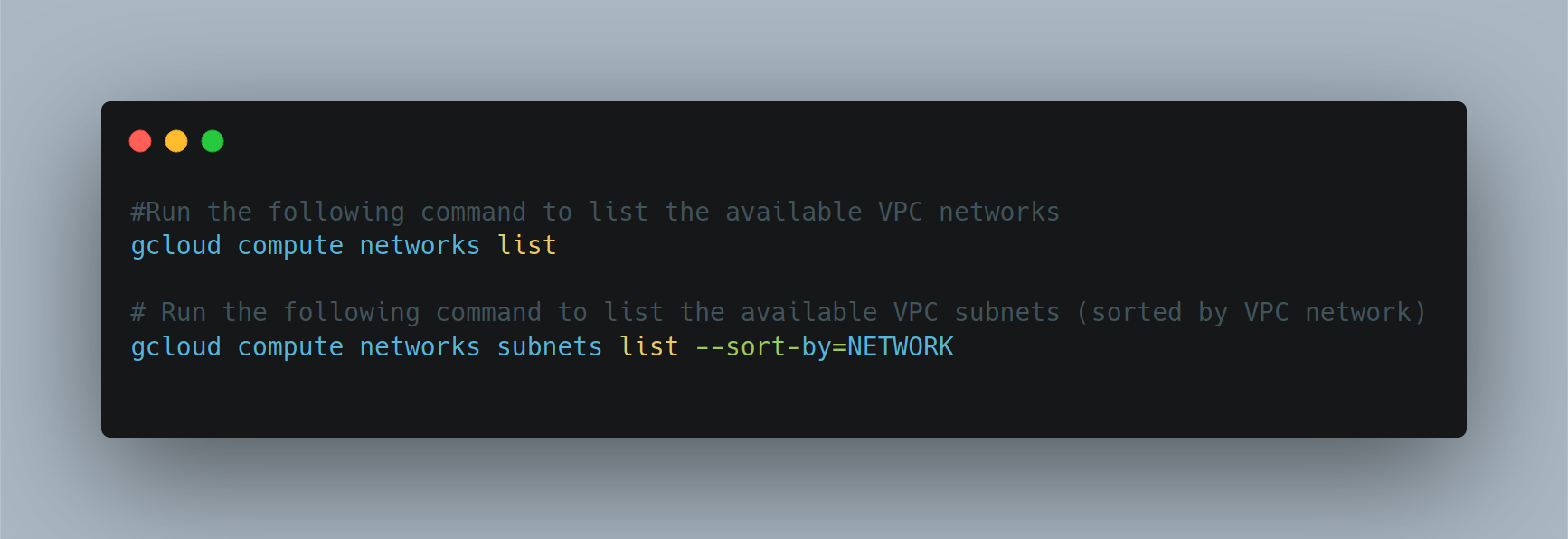
default and mynetwork are auto mode networks, whereas, managementnet and privatenet are custom mode networks. Auto mode networks create subnets in each region automatically, while custom mode networks start with no subnets, giving you full control over subnet creation
Let's add some firewall rules in both Virtual Network.
- Navigate to Navigation menu > VPC network > Firewall.
- Click + Create Firewall Rule.
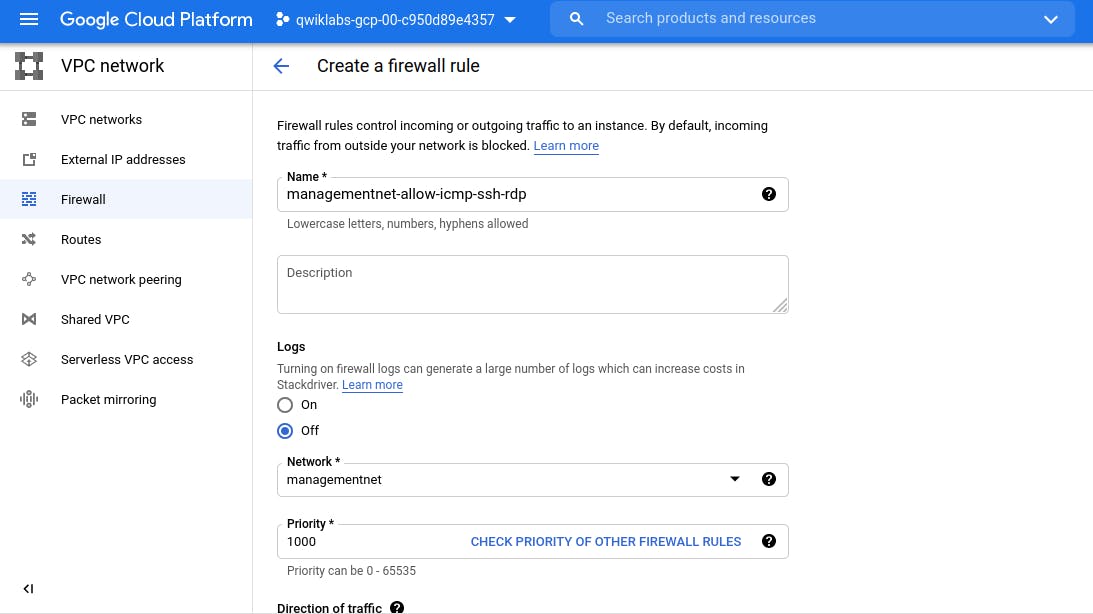
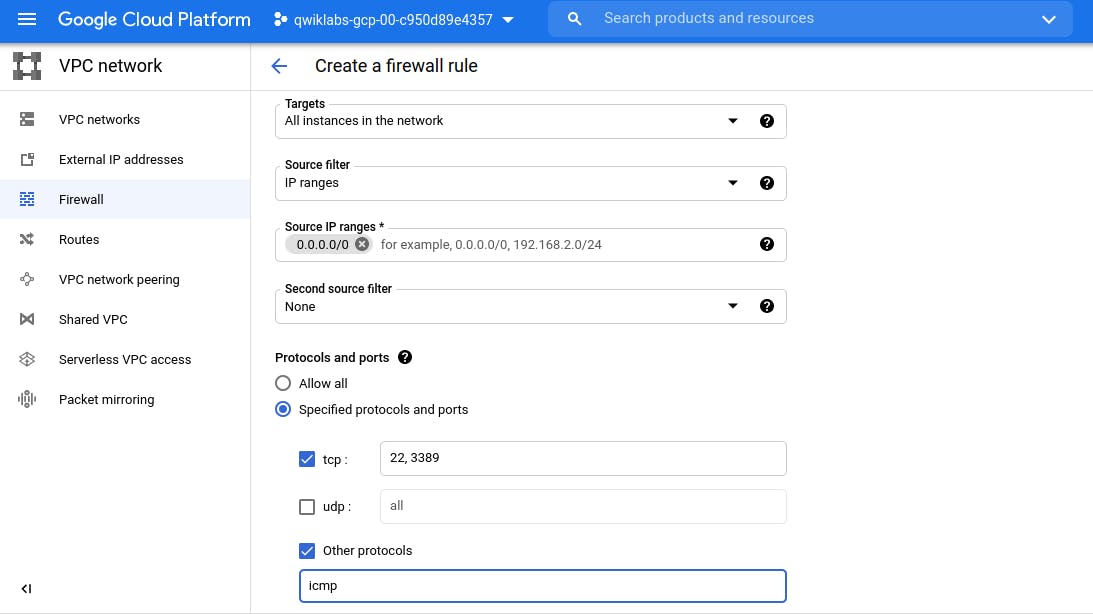
Firewall settings for 'managementnet' virtual network
Name managementnet-allow-icmp-ssh-rdp
Network managementnet
Targets All instances in the network
Source filter IP Ranges
Source IP ranges 0.0.0.0/0 (Make sure to include the /0 in the Source IP ranges to specify all networks. )
Protocols and ports Specified protocols and ports, and then check tcp, type: 22, 3389; and check Other protocols, type: icmp.
Same settings will be for 'privatenet' virtual network, just network and name will be different.
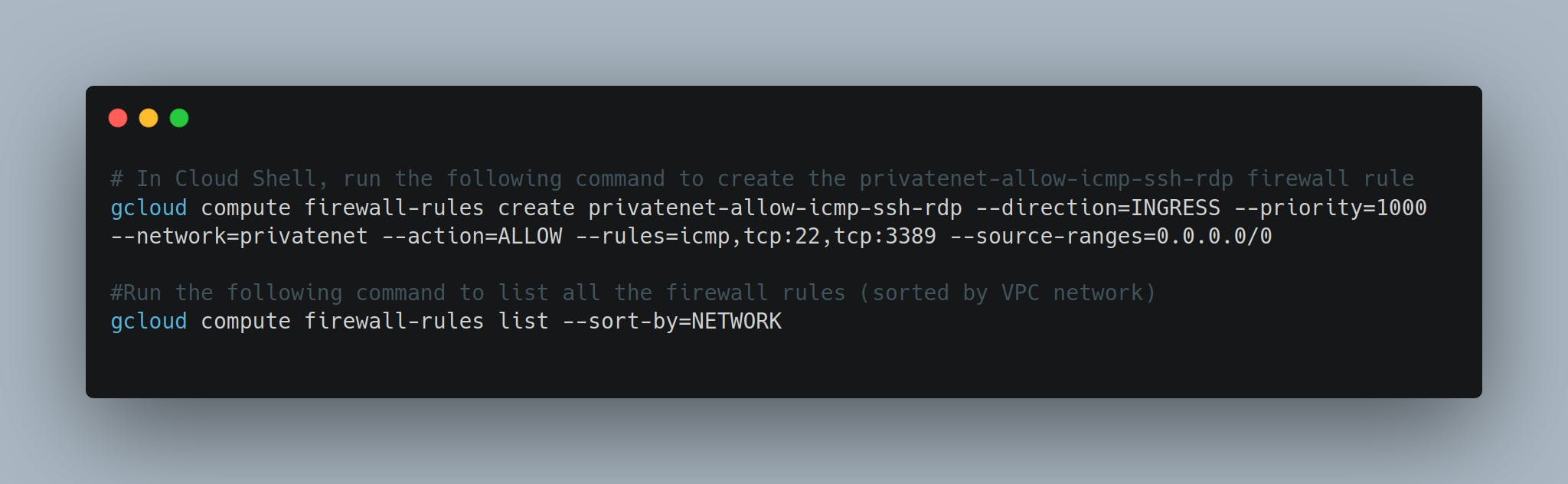
You can create using below command as well.
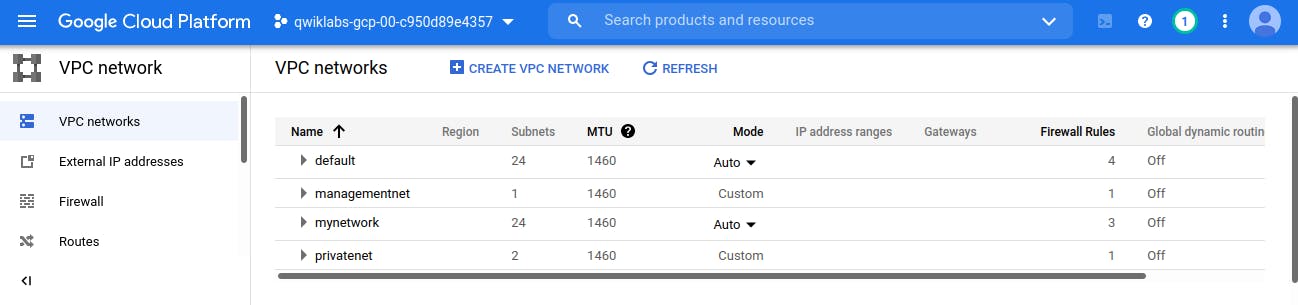
We could see value '1' under firewall column for both virtual network which is created by us.
Let's see the ports
Port 22 The standard TCP port for SSH is 22. SSH is generally used to access Unix-like operating systems, but it can also be used on Microsoft Windows. Windows 10 uses OpenSSH as its default SSH client and SSH server.
Port 3289 UDP (User Datagram Protocol) port 3289 uses the Datagram Protocol, a communications protocol for the Internet network layer, transport layer, and session layer. This protocol when used over PORT 3289 makes possible the transmission of a datagram message from one computer to an application running in another computer.
ICMP Internet Control Message Protocol (ICMP) is used to send control messages to network devices and hosts.
Till now, we have created virtual network (managementnet and privatenet) and add firewall rules to both
Let's create Virtual Machine or Virtual Instance in Both Virtual Network
Create two VM instances:
- managementnet-us-vm in managementsubnet-us
- privatenet-us-vm in privatesubnet-us
- Navigate to Navigation menu > Compute Engine > VM instances.
- Click Create instance
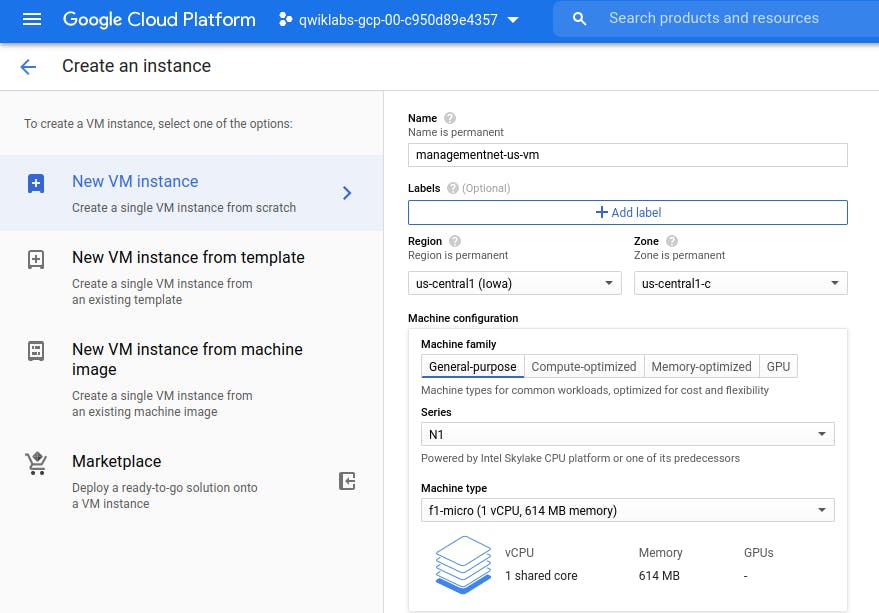
Select the network in which you want to create virtual machine, (else, it will create under default network)
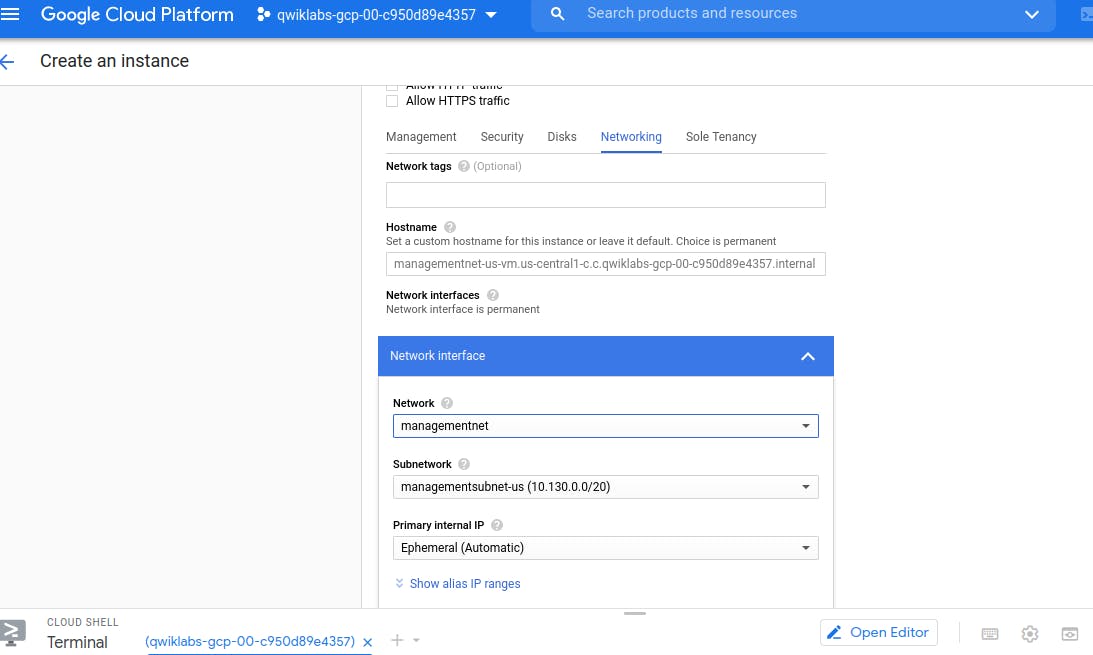
Similarly Create the privatenet-us-vm instance
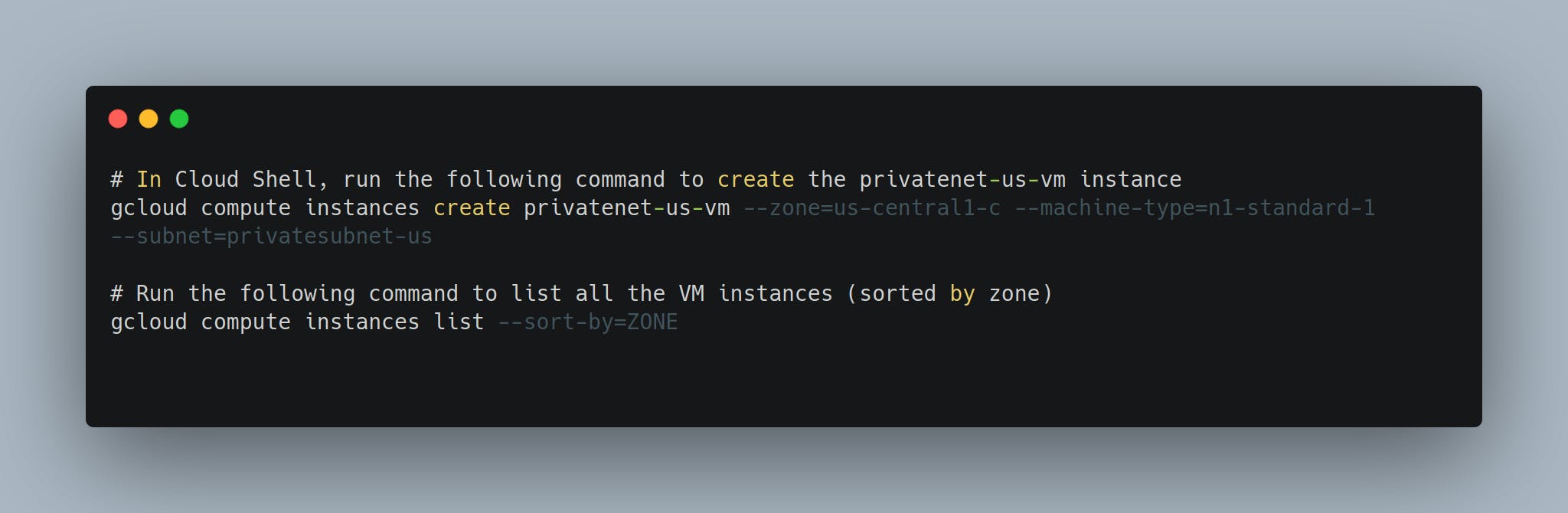
Now we have everything ready
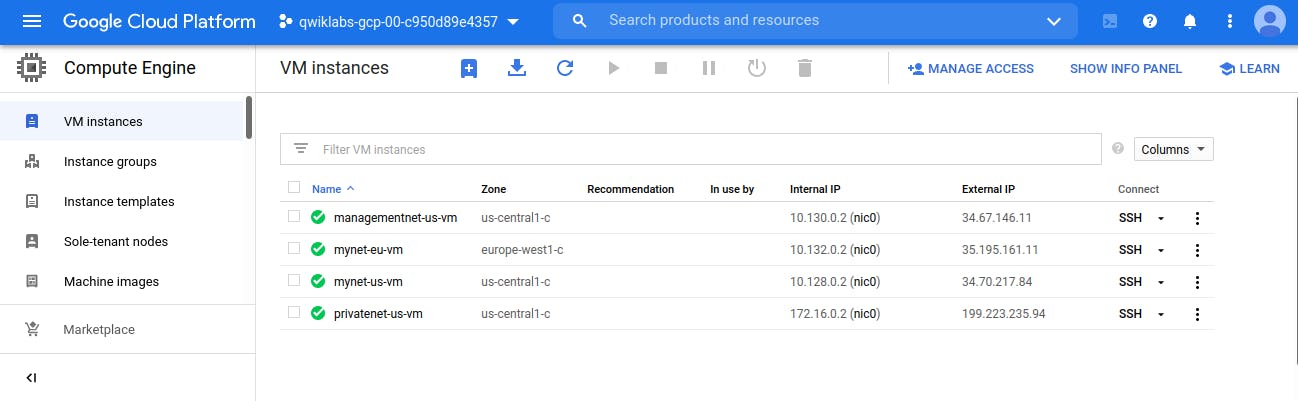
Explore the connectivity between VM instances
Virtual Networks, Firewall Rules, Virtual Machine in the Virtual network. Now, Let's test whether we can access the Virtual Network. and also can we access the Virtual Machine from other virtual network.
Ideally, we should able to access the Virtual Network (Public IP address) But we should not able to access the Private IP address of Virtual Network form other Virtual Network.
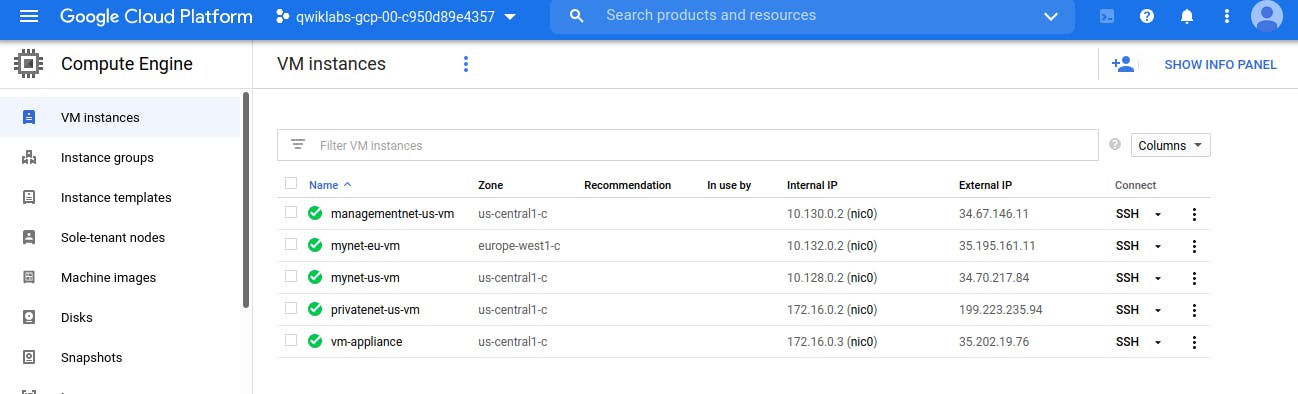
Note the external IP addressees for mynet-eu-vm, managementnet-us-vm, and privatenet-us-vm.
For mynet-us-vm, click SSH to launch a terminal and connect.
To test connectivity to mynet-eu-vm's external IP, run the following command, replacing mynet-eu-vm's external IP:
ping -c 3 ip (i.e. ping that particular IP address and stop after 3 count replies)
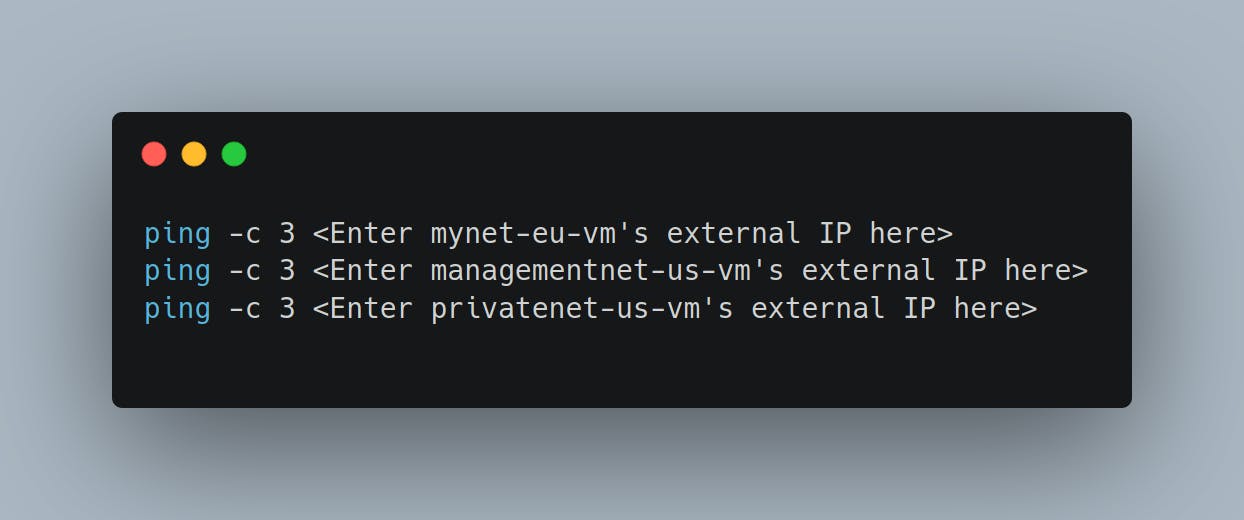
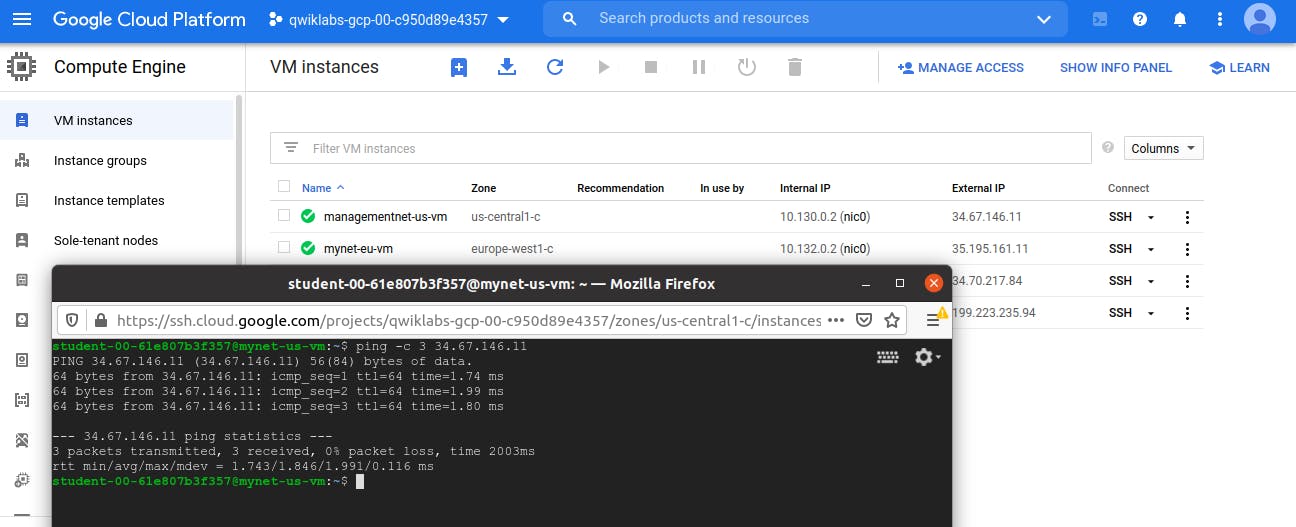
You are able to ping the external IP address of all VM instances, even though they are either in a different zone or VPC network. This confirms public access to those instances is only controlled by the ICMP firewall rules that you established earlier.
Ping the internal IP addresses
Note the internal IP addressees for mynet-eu-vm, managementnet-us-vm, and privatenet-us-vm.
Return to the SSH terminal for mynet-us-vm.
To test connectivity to mynet-eu-vm's internal IP, run the following command, replacing mynet-eu-vm's internal IP:
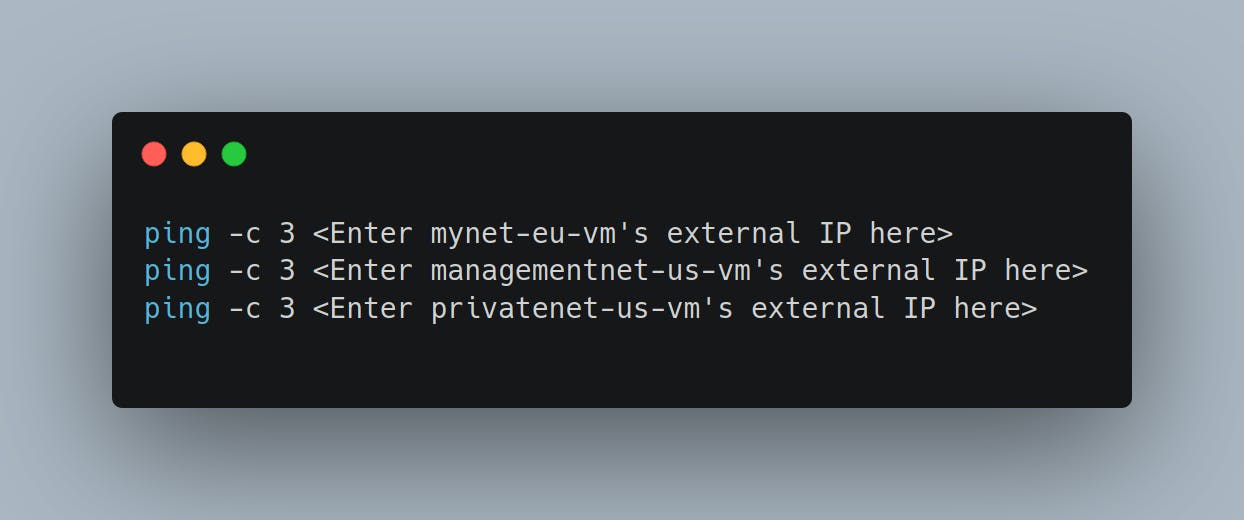
You are able to ping the internal IP address of mynet-eu-vm because it is on the same VPC network as the source of the ping (mynet-us-vm), even though both VM instances are in separate zones, regions and continents!
You are unable to ping the internal IP address of managementnet-us-vm and privatenet-us-vm because they are in separate VPC networks from the source of the ping (mynet-us-vm), even though they are all in the same zone us-central1.
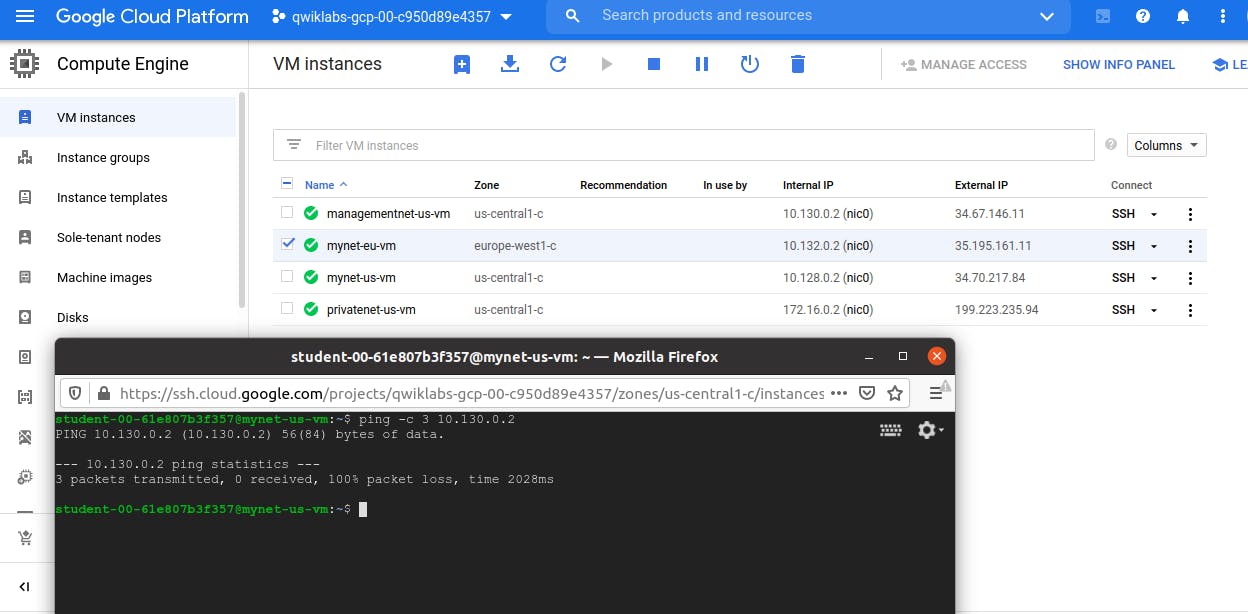
VPC networks are by default isolated private networking domains. However, no internal IP address communication is allowed between networks, unless you set up mechanisms such as VPC peering or VPN.
Let's Create a VM instance with multiple network interfaces
Create the vm-appliance instance with network interfaces in privatesubnet-us, managementsubnet-us and mynetwork. The CIDR (Classless inter-domain routing) ranges of these subnets do not overlap, which is a requirement for creating a VM with multiple network interface controllers (NICs).
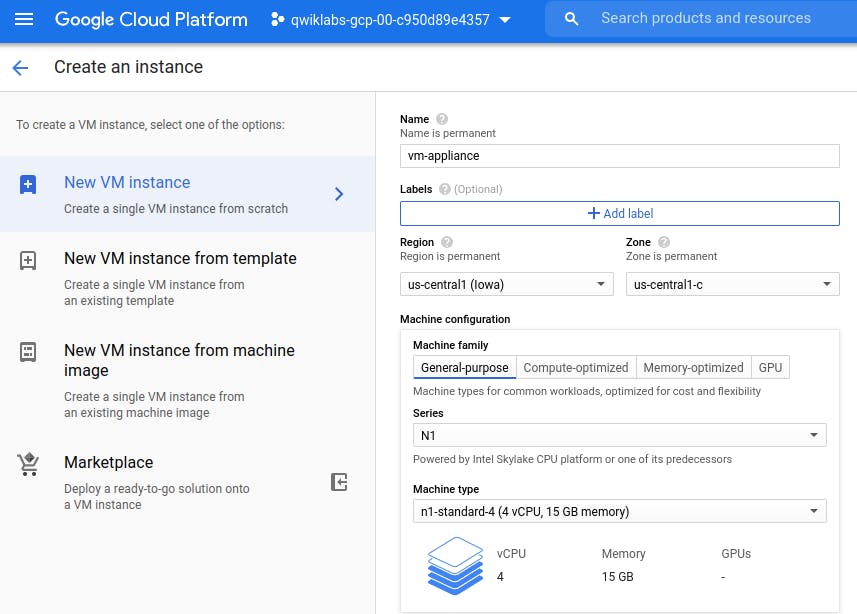
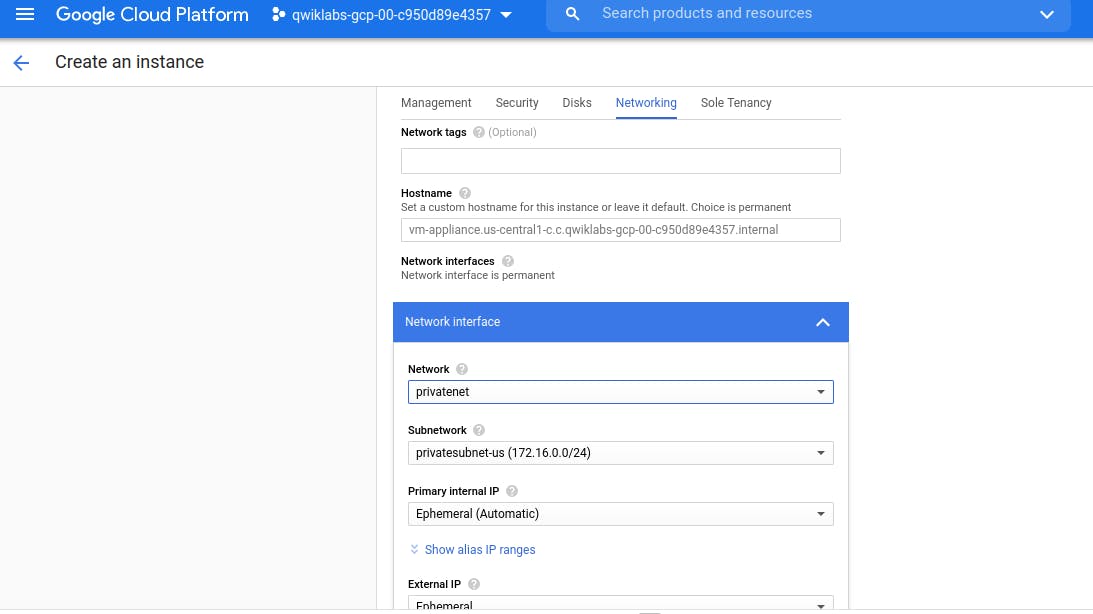
Similarly add other Network Interface, by clicking on 'Add Network Interface'
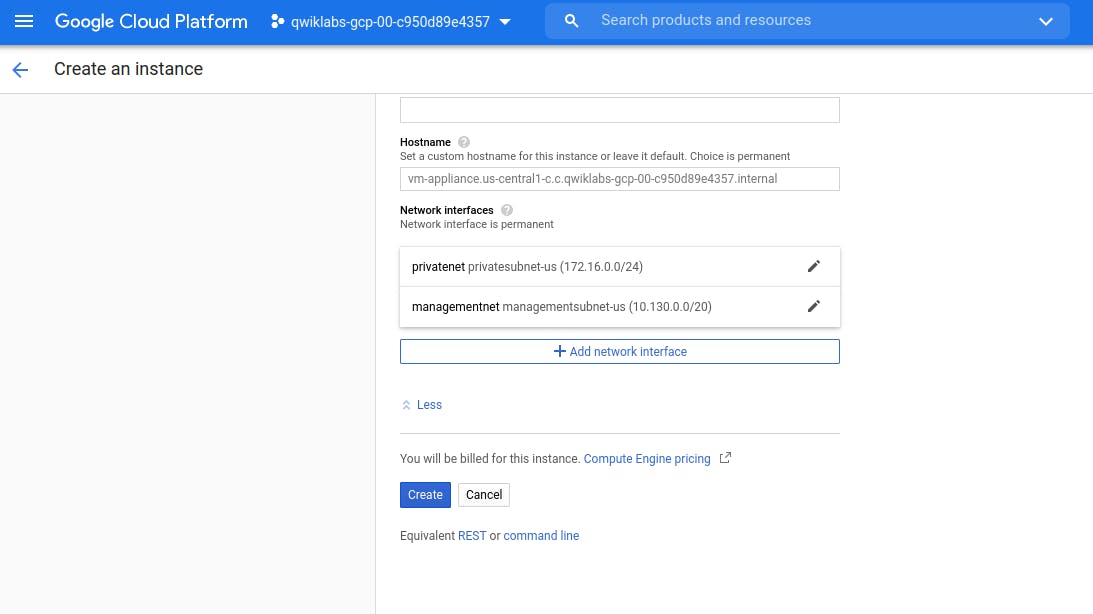
Click on nic0 to explore all Network Interface linked with this Virtual Machine.
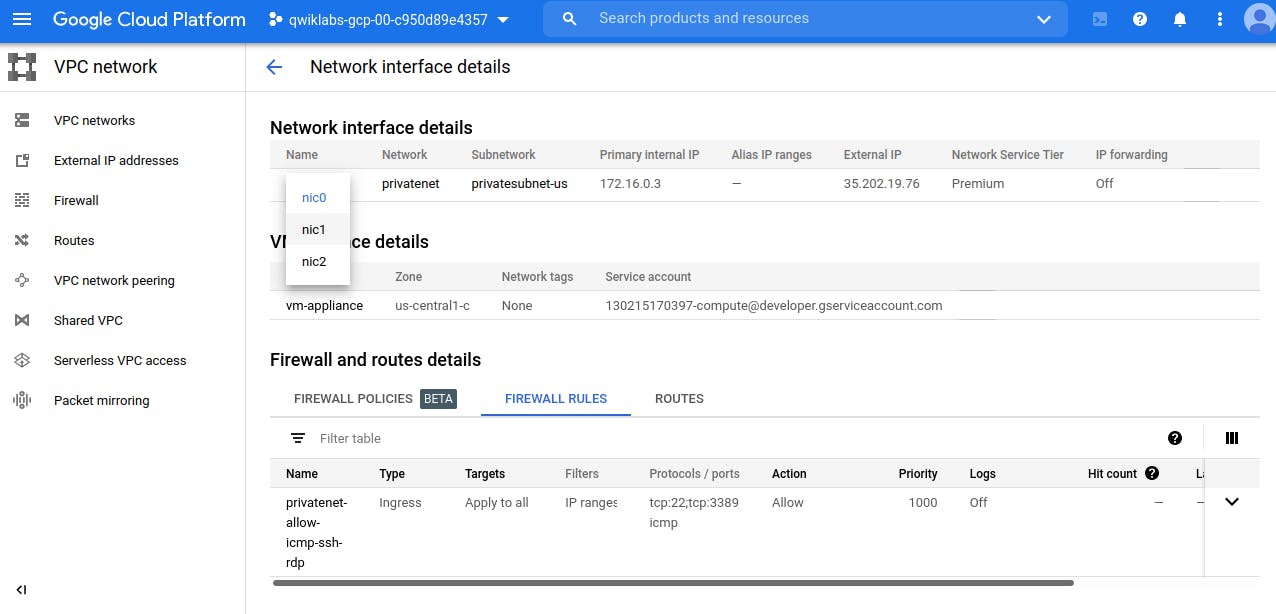
For vm-appliance, click SSH to launch a terminal and connect.
Run the following, to list the network interfaces within the VM instance:
sudo ifconfig
The sudo ifconfig command lists a Linux VM's network interfaces along with the internal IP addresses for each interface.
Note the internal IP addressees for privatenet-us-vm, managementnet-us-vm, mynet-us-vm, and mynet-eu-vm.
Return to the SSH terminal for vm-appliance.
To test connectivity to privatenet-us-vm's internal IP, run the following command, replacing privatenet-us-vm's internal IP:
ping -c 3 <Enter privatenet-us-vm's internal IP here> ping -c 3 privatenet-us-vm You are able to ping privatenet-us-vm by its name because VPC networks have an internal DNS service that allows you to address instances by their DNS names rather than their internal IP addresses.
ping -c 3 <Enter mynet-us-vm's internal IP here>
This will work!
ping -c 3 <Enter mynet-eu-vm's internal IP here>
This does not work! In a multiple interface instance, every interface gets a route for the subnet that it is in. In addition, the instance gets a single default route that is associated with the primary interface eth0. Unless manually configured otherwise, any traffic leaving an instance for any destination other than a directly connected subnet will leave the instance via the default route on eth0.
Resource googlecourses.qwiklabs.com - GSP211